Microsoft Entra ID data store integration
You can integrate the Microsoft Entra ID (formerly Azure AD) data store with Arculix.
With this Microsoft Entra ID data store integration in Arculix, you can configure a data store for each tenant in Arculix. Users can log in using their Microsoft Entra ID accounts with single sign-on (SSO) to SAML and OpenID applications.
Arculix supports the following data store types:
Active Directory (AD) – Integrate your AD data store with Arculix by using an Arculix LDAP Agent on-prem or in the cloud.
Arculix Directory – Our proprietary directory system designed to meet our customer's specific needs.
Microsoft Entra ID – Integration information for Microsoft Entra ID with Arculix is described in this document.
When users log in to the Arculix SSO portal, they can enter their Microsoft Entra ID credentials. Or, they can use the Arculix Mobile app to scan the QR code of the SSO portal for a passwordless experience.
These credentials are then checked against Microsoft Entra ID via API through the SecureAuth Connector. Arculix can check if a user is in a group in Microsoft Entra ID. Then, it can precisely decide how to apply the Arculix MFA policy. The pass-through mechanism simplifies logging in, making it faster and easier for users.
With the Microsoft Entra ID integration in Arculix, it has the following capabilities:
User look up
Groups look up
Pass-through authentication
It is important to know that integrating with Microsoft Entra ID has many benefits. However, there are still some limitations:
Arculix can search for users in either AD or Microsoft Entra ID, but not both at the same time.
You can use different directories for your organization, but it's best to connect them to separate domains.
Arculix does not support password management for user accounts in Microsoft Entra ID.
Prerequisites
Have Microsoft Entra ID configured for integration with Arculix. See Microsoft Entra ID configuration.
Provide the following values to SecureAuth Support:
Application secret key
Application (client) ID
Directory (tenant) ID
Domain name
Add Microsoft Entra ID data store in Arculix
We are working hard to bring the Microsoft Entra ID data store connection settings to the Arculix UI. For now, check the Prerequisites for the Microsoft Entra ID values. You'll need to provide these to SecureAuth Support.
After the SecureAuth team sets it up, you can use Microsoft Entra ID as your organization's directory in Arculix. Make sure your Microsoft Entra ID domain is set in your Arculix organization settings.
Work with SecureAuth Support to add and configure the Microsoft Entra ID data store in Arculix.
Then, you can configure your Arculix applications and policies to control access for users and groups in Microsoft Entra ID.
Set group restriction in Arculix applications
In Arculix, each SAML Service Provider and OpenID Connect application has a Security tab.
This tab lets you manage access for certain user groups. With Microsoft Entra ID as a new directory, you can select the directory type and grant access to the application on the Security tab.
In Arculix, from the left navigation, click Applications.
For the application you want to configure, click the Edit pencil icon.
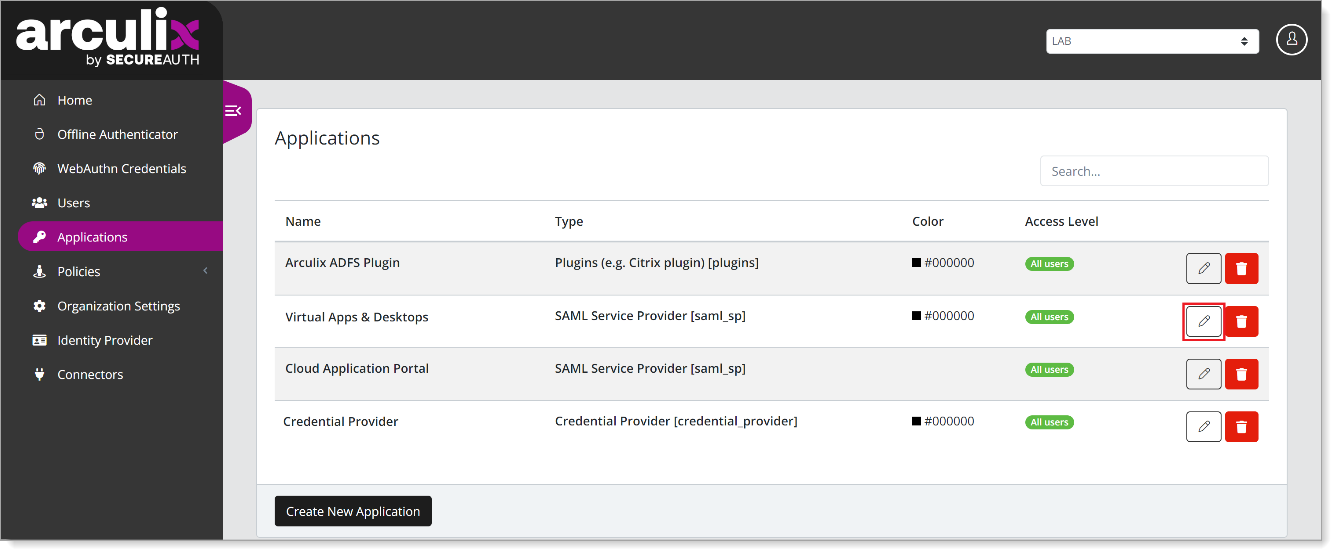
Select the Security tab, set the Group Permissions to Restricted to Selected Groups.
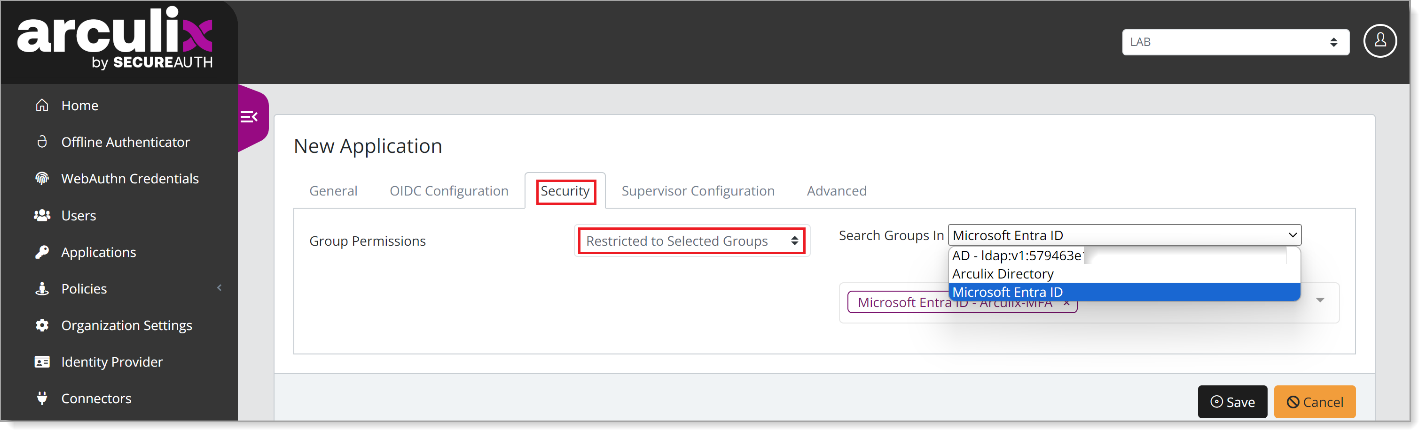
From the Search Groups in list, select Microsoft Entra ID and find the group you want to give application access to.
Save your changes.
Set group condition in a policy
The policy engine in Arculix allows you to set actions for specific conditions and events. To learn more about configuring a policy, see Manage policies.
A new Directory Groups setting allows you to set Microsoft Entra ID as specific condition in a policy.
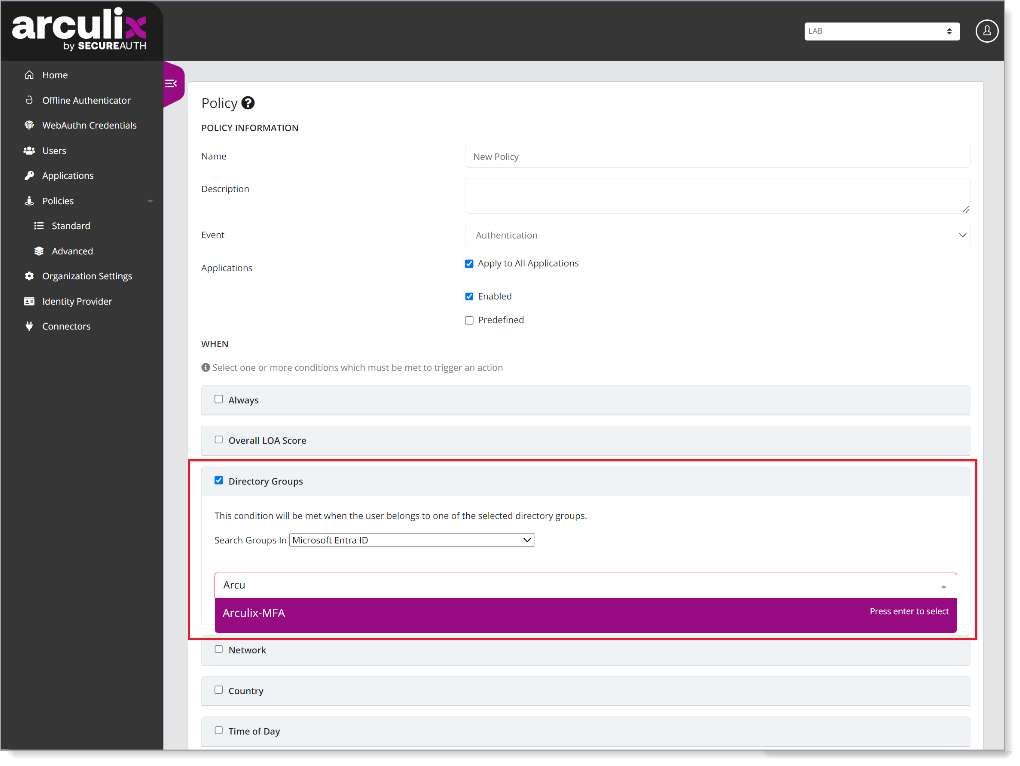 |
Map attributes in SAML applications
For some SAML integrations, you need to include Asserted Attributes and set authentication values for the application.
Like what you might have done with Active Directory, you can set up the attribute assertion for Microsoft Entra ID.
To learn more about adding Asserted Attributes, see step 5 in the Arculix SAML configuration integration guide.
Some attribute mapping examples:
Friendly Name | Name | Value |
|---|---|---|
|
|
|
|
|
|
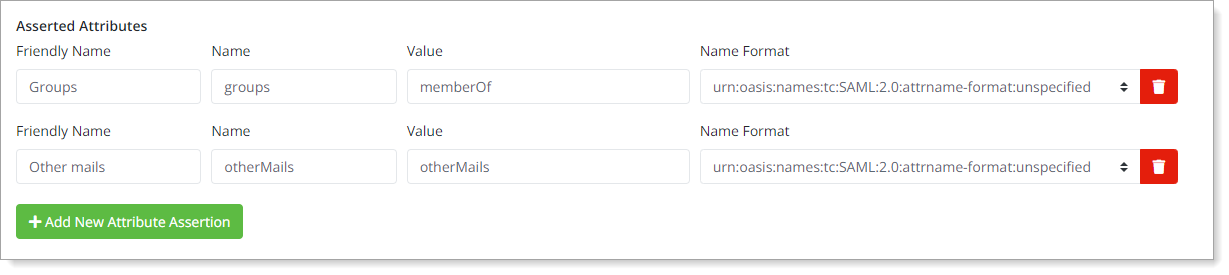 |
Examples of asserted attributes